We are excited to announce the release of A Developer’s Guide to FAPI. This comprehensive ebook provides the technical breakdown necessary to understand, implement, and confidently deploy the high-assurance security profile mandated by regulated ecosystems worldwide, from Open Banking to e-Health.
What Is FAPI and Why Is It Necessary?
For architects and engineers who have built systems on the foundation of OAuth 2.0 and OpenID Connect (OIDC), the power of delegated access is clear. However, the base OAuth 2.0 specification is a flexible framework, not a strict protocol. Its flexibility leaves many critical security decisions to the implementer: the appropriate flow, client authentication methods, and token type, just to name a few.
For systems handling high-stakes data — be it life savings, medical records, or legally binding contracts — the "it depends" nature of standard OAuth 2.0 is an unacceptable security risk.
This is the exact problem the FAPI Security Profile was created to solve. FAPI is a set of rigorous, prescriptive security and interoperability rules that extend and harden the base OAuth 2.0 and OIDC frameworks. FAPI is not a new protocol; it is a profile that eliminates risky options and mandates a secure-by-default configuration.
The FAPI Paradigm Shift
FAPI defines a fundamental change in how access tokens are treated, shifting the security burden away from relying on passive token secrecy and towards active, cryptographic proof of identity. This paradigm shift secures the access token itself and hardens the issuance process. In addition, the Resource Server’s role moves from a “simple” token validator to a client identity verifier.
Protecting the access token with Mutual TLS (mTLS) and Demonstration of Proof-of-Possession (DPoP)
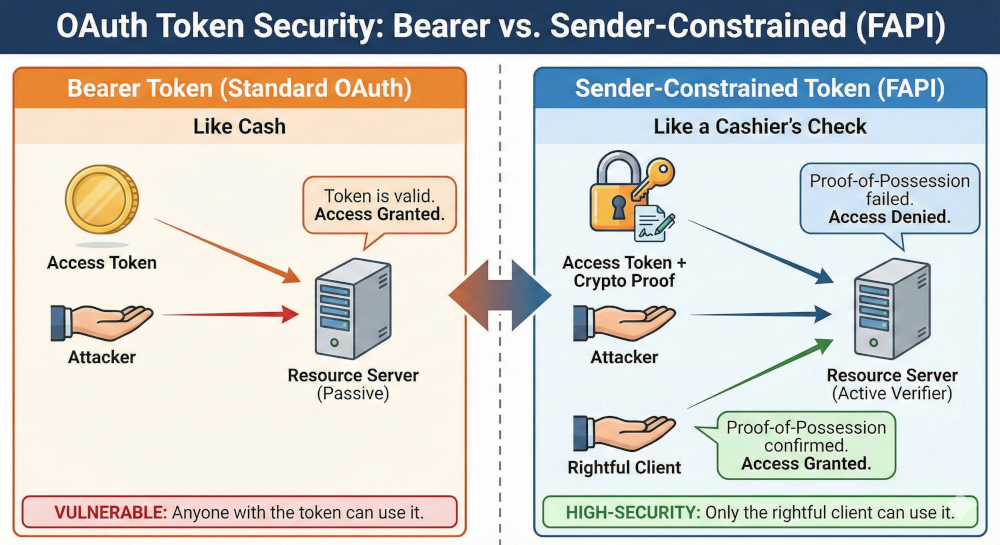
If there is one core concept that defines FAPI, it is the move from the bearer model to a sender-constrained model for access tokens.
A standard bearer token is like cash. If a thief steals the token (via XSS, database breach, or a compromised network), they can use it immediately because the Resource Server only checks if the token is valid, not who is presenting it.
A FAPI-compliant, sender-constrained token is fundamentally different. It is cryptographically bound to the specific, confidential client that requested it, making it like a cashier's check made out to a specific person. If stolen, the thief cannot cash it because they cannot prove their identity as the rightful owner.
The guide provides an in-depth look at the two first-class mechanisms for achieving this level of security: Mutual TLS (mTLS) and Demonstration of Proof-of-Possession (DPoP).
Protecting the issuance flow with Pushed Authorization Requests (PAR)
The sender-constrained model secures the resulting asset (the access token). FAPI also secures the process of issuance itself, preventing an attacker from getting a token in the first place.
The guide details the dual mechanisms that protect token issuance: Asymmetric Client Authentication and PAR.
In a standard OAuth 2.0 flow, the authorization request is initiated by a large, complex GET request through the user’s browser. This is the weakest link, exposing sensitive parameters (scopes, identifiers, and PKCE challenges) to browser history, server logs, and, critically, the Referer header.
PAR is the FAPI 2.0 mandated solution where the client's backend sends the authorization request parameters to the Authorization Server's /par endpoint in a secure POST body, receiving a request_uri in return. This process enhances confidentiality, overcomes URL length limits, and enables early client authentication for improved robustness and fraud detection.
The Resource Server’s burden of proof
The ebook dedicates an entire chapter to the Resource Server's transformed role, emphasizing that in a FAPI ecosystem, the Resource Server is no longer a passive "ticket-taker". It becomes an active security guard that must enforce the burden of proof.
After performing all standard checks (signature, expiry, audience, and scope), the Resource Server must perform the final, mandatory sender-constraint check: Is the entity presenting this token the same one it was issued to?
This responsibility is what renders stolen FAPI tokens useless, ensuring the high-value data remains secure.
Why You Must Get This Guide Now
The complexity of FAPI lies not in any single mechanism, but in correctly implementing the complex, interlocking logic across the Authorization Server, Client, and Resource Server.
By mandating a secure blueprint and drastically reducing protocol optionality, FAPI solves the "NxM integration problem" of standard OAuth 2.0. This strictness is enforced by the OIDF Conformance Test Suite.
If you are a developer or architect operating in any regulated sector or simply building the highest tier of security, FAPI compliance is non-negotiable.
This guide is your critical roadmap, allowing you to move beyond the fragile flexibility of standard OAuth 2.0, master the FAPI blueprint, and establish the security gold standard for your applications.
Download "A Developer's Guide to FAPI" now and confidently tackle the next generation of identity security challenges.
About the author

Andrea Chiarelli
Principal Developer Advocate
I have over 20 years of experience as a software engineer and technical author. Throughout my career, I've used several programming languages and technologies for the projects I was involved in, ranging from C# to JavaScript, ASP.NET to Node.js, Angular to React, SOAP to REST APIs, etc.
In the last few years, I've been focusing on simplifying the developer experience with Identity and related topics, especially in the .NET ecosystem.