Before you start
To use this feature, your Auth0 plan or custom agreement must include Enterprise Connections. To learn more, read Auth0’s Pricing Page.To test an inbound SCIM connection, you need to install Postman locally.
Configure SCIM settings in Auth0
- From the Auth0 Dashboard, go to Authentication > Enterprise > SAML > [your-connection] > Provisioning.
- Toggle Sync user profiles using SCIM to on. This opens a new section on the same page with additional configuration.
- In the Mapping tab, set SCIM attribute containing the User ID to userName.
- In the Additional Mappings section, enter the following JSON:
You can also view the attribute mapping and make sure the extended SCIM attributes are mapped to your preferred Auth0 attributes.
- When you’re done, select Save Changes.
Retrieve SCIM endpoint URL and token
To configure SCIM in a Microsoft Entra ID tenant, you need a SCIM endpoint URL and token from Auth0. You can get these values from the Auth0 Dashboard:- From the Auth0 Dashboard, go to Authentication > Enterprise > SAML > [your-connection] > Provisioning.
- In the Sync user profiles using SCIM > Setup section, copy the SCIM Endpoint URL.
- In the same section, under Bearer Token, select Generate New Token. Choose the token’s expiration date and scopes, then select Generate Token. The default requires scopes used by Azure AD are
get:users,post:users,patch:users, anddelete:users. - Copy the bearer token. For security, this is the only time the token is visible.
/v2/connections/{id}/scim-configuration/tokens.
For best practices, read the Configure Inbound SCIM deployment guidelines.
Configure SCIM in Entra ID for SAML Apps
If your SAML application is not already registered, follow Configure IdP-Initiated SAML Login with Azure as the IdP to register a custom, non-gallery enterprise application in an Entra ID tenant. Then, to configure SCIM:- From the Microsoft Entra admin center, go to Entra ID > Enterprise apps > [your-application].
- Go to Manage > Properties and set Assignment Required to Yes.
- Go to Manage > Users and Groups and assign the Azure AD users you want to provision. When you assign a group, the users from that group are provisioned.
- Go to Manage > Provisioning and select Get started.
- Set the Provisioning Mode to Automatic.
- Expand the Admin Credentials section and configure the following parameters:
- Set the Tenant URL field to the SCIM endpoint URL you saved in the previous step, and append the query parameter
?aadOptscim062020to the end of the URL. This is Microsoft’s recommended workaround for a known SCIM 2.0 issue. - Set the Secret Token to the token value you saved in the previous step, then select Save.
- Set the Tenant URL field to the SCIM endpoint URL you saved in the previous step, and append the query parameter
- Expand the Mappings section, then select Provision Azure Active Directory Users to open the Attribute Mapping screen.
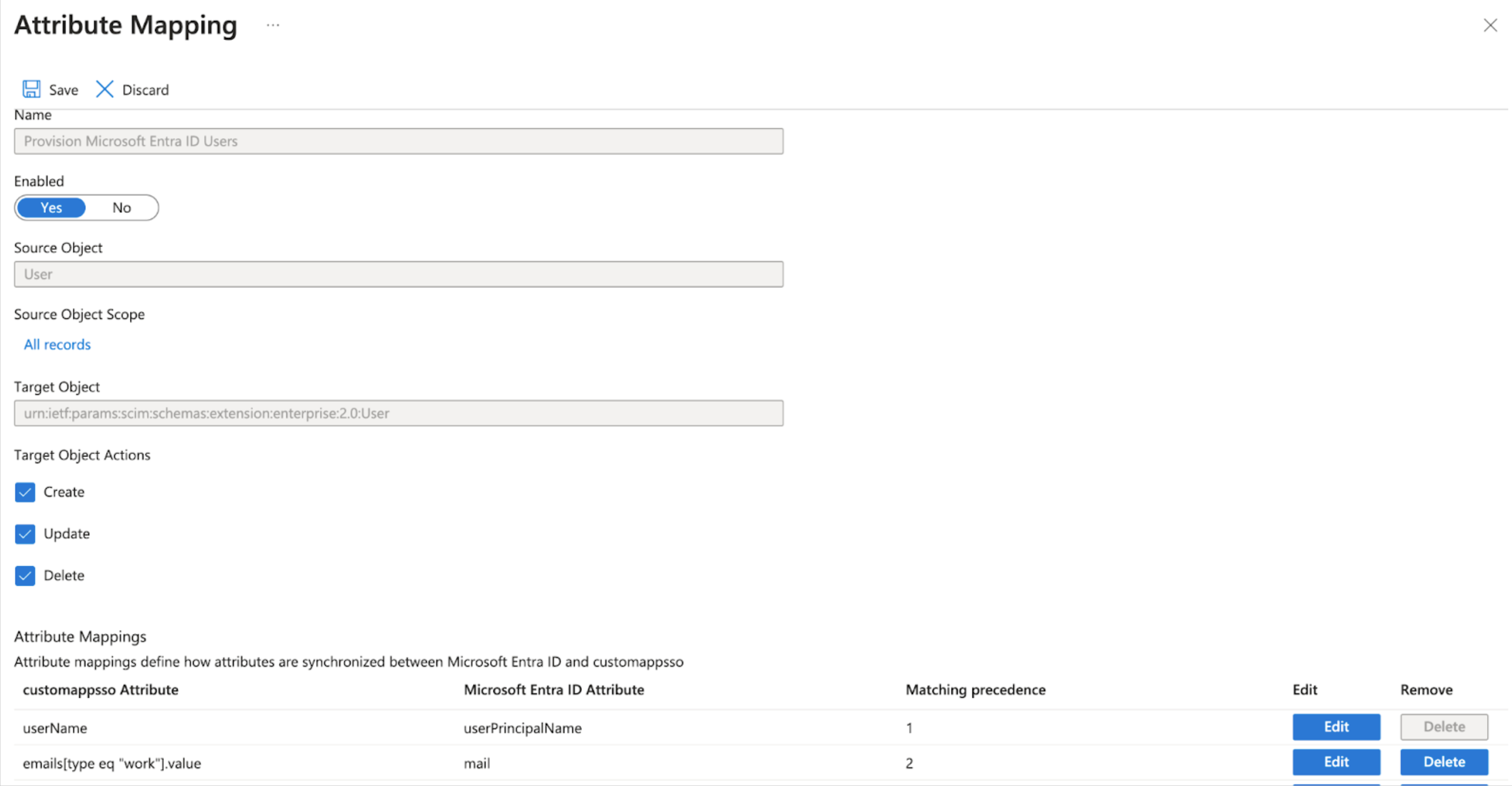
- In the attribute mapping table row containing
emails[type eq "work"].valueandmail, select Edit to go to the Edit Attribute screen and configure the following parameters:- Set Match objects using this attribute to Yes.
- Set Matching precedence to 2.
- Select OK to save the configuration. This closes the Edit Attribute screen. Then, on the Attribute Mapping screen, select Save.
Testing
- On the Enterprise application overview screen, go to Manage > Provisioning > Provision on Demand to test the SCIM connection.
- Go to Select a user or group and enter the name of a user that you assigned to the application, then select the user and choose Provision. This creates the user in the Auth0 tenant.
- Set the Provisioning Status to On in order to provision all assigned users.

