Configure Active Directory
- Go to Auth0 Dashboard > Authentication > Enterprise > Active Directory/LDAP, and select the connection you want to configure.
- Enable the Use Windows Integrated Auth (Kerberos) switch.
Auto-detected range for Kerberos
When Kerberos authentication is enabled, the visible IP address of the server where the AD Connector is running is implicitly added to the network IP range. This means that if a user’s requests originate from the same visible IP address as that of the AD Connector, then Kerberos authentication will be attempted.- Configure the IP Ranges. Use CIDR-notation. These should be ranges that are visible by Auth0. When Auth0 is running in the cloud, it won’t be able to see your user’s internal IP address. In that case you’d configure the public facing/WAN IP address(es) of your company.
- We recommend restarting the Windows Service that hosts the AD Connector every time this setting is changed. This way, changes will take effect immediately.
Authentication flow
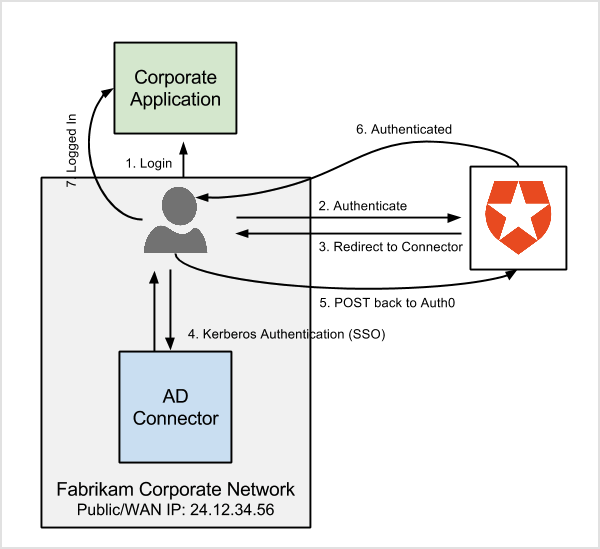
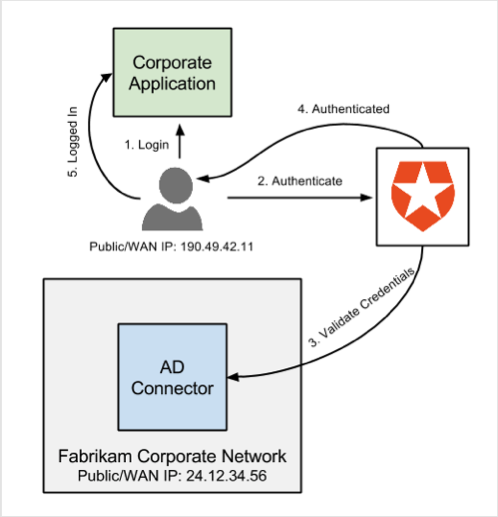
Depending on the users’ location, the authentication flow will be different when IP ranges are set. Using Fabrikam as an example, since it uses the SaaS version of Auth0, they configured their Public IP Address (24.12.34.56/32) in the connection. Users connecting from within the building will all originate from 24.12.34.56 (as configured on the connection). When they authenticate, the users can follow the AD/LDAP native flow and have a seamless experience.
For this to work, the network must allow the users to connect to the AD/LDAP Connector on the port configured in the config.json file. In highly available deployments of the Connector, the address users will be connecting to is the network load balancer in front of all connectors instances.
Auto-login with Lock
Detecting IP ranges in an AD/LDAP connection and using those ranges with Lock to allow integrated Windows Authentication is a feature that works in Lock 10, but can only be used in Lock 11 in Universal Login scenarios. This feature is disabled in Lock 11 when Lock 11 is used in Embedded Login scenarios.
Bypass Kerberos at runtime
You can prevent Kerberos from being used, even if the user is logging in from an IP address within the range configured in the connection’s settings, by passingrememberLastLogin: false to lock.show().
Enable Kerberos request logging
- To enable verbose logging of Kerberos requests, add a system level environment variable
DEBUG=kerberos-server. - Restart the Connector.
- Log in again and check the logs for more information.
Firefox support for Kerberos
By default, Firefox rejects all “negotiate” requests required to authenticate users with Kerberos. If you wish to use Firefox with Kerberos, you need to AllowList the server where the connector is installed.- Open a Firefox tab and type
about:configin the address bar. - Dismiss any warning message, and in the search box type
negotiate. - Locate the
network.negotiate-auth.trusted-urisitem and double click to change its value. - Type the domain name of the server where the connector is installed. If you have multiple instances of the connector behind a load balancer, add the dns name of the balancer.
The value accepts a comma-separated list of URL prefixes or domains in the form of
mydomain.com, https://myotherdomain.com. - Click Ok. You don’t need to restart the server for the changes to take effect.
HTTPS support for Kerberos
Kerberos authentication works over HTTP (not HTTPS). Microsoft Office 365 and other modern products might not work with HTTP. To resolve this limitation:- Set up a reverse proxy and expose the AD/LDAP Connector on an HTTPS domain. You can use the
SERVER_URL(Front Facing URL) parameter to publish the public location where the AD/LDAP Connector will be listening to incoming requests. - Map the
SERVER_URLin the reverse proxy to all internal instances of the deployed connectors.

