This integration, now generally available, enables organizations using Okta Workforce Identity as their Identity provider (IdP) to log users out of Auth0-powered applications whenever a logout or de-provisioning event occurs in Okta Workforce Identity. Auth0 customers can now leverage this feature in their Auth0-powered applications and significantly improve their customer organization's security.
What Is Okta Universal Logout?
Universal Logout is a feature of Okta Identity Threat Protection (ITP), a capability of Okta Workforce Identity that leverages AI to detect and automate responses to identity threats. When ITP detects elevated risk for a given user, it can invoke Universal Logout to log the user out of the applications they are using.
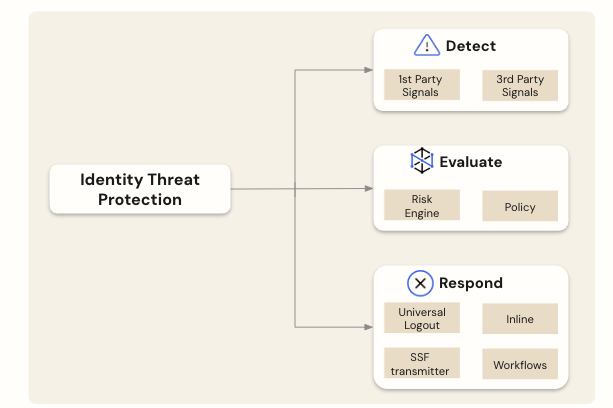
Built on the Global Token Revocation standard, Universal Logout goes beyond the established OpenID Connect logout standards by revoking refresh tokens in addition to session cookies. This provides a comprehensive logout solution that spans across:
- Traditional web applications
- Browser-based JavaScript applications such as Single-Page Applications (SPAs)
- Native applications that use a mix of application sessions, identity provider sessions, and refresh tokens to keep the user authenticated
Today, Okta Workforce Identity customers can use Identity Threat Protection and Universal Logout with popular SaaS apps like Google Workspace, Apple Business Manager, Microsoft Office 365, Salesforce, Slack, and Zoom. For other applications to work with it, developers would need to build a Global Token Revocation endpoint as described in Build Universal Logout for your app.
Auth0 Now Supports Global Token Revocation Endpoints out-of-the-box
Auth0 customers federating with Okta Workforce Identity using the Okta, SAML, or OpenID Connect connection types no longer need to build a global token revocation endpoint. Instead, with minimal configuration required, they can provide the Okta admin with Auth0’s connection-specific endpoint URL, as shown below:
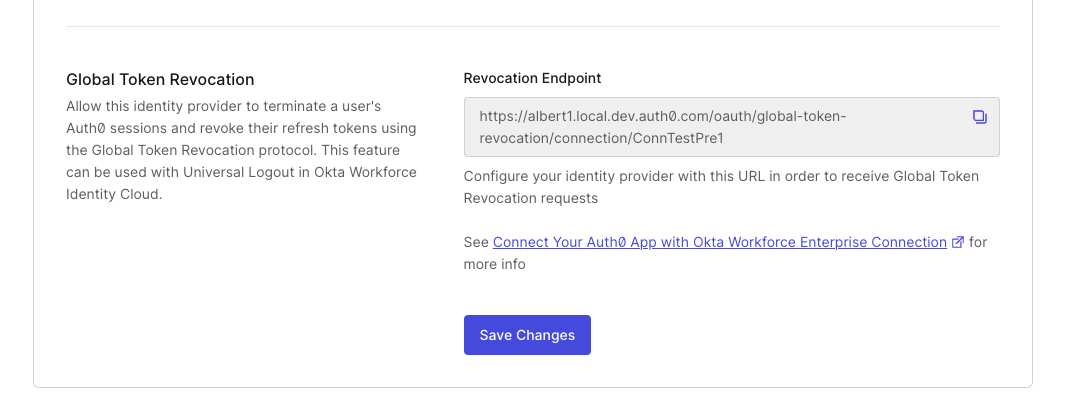
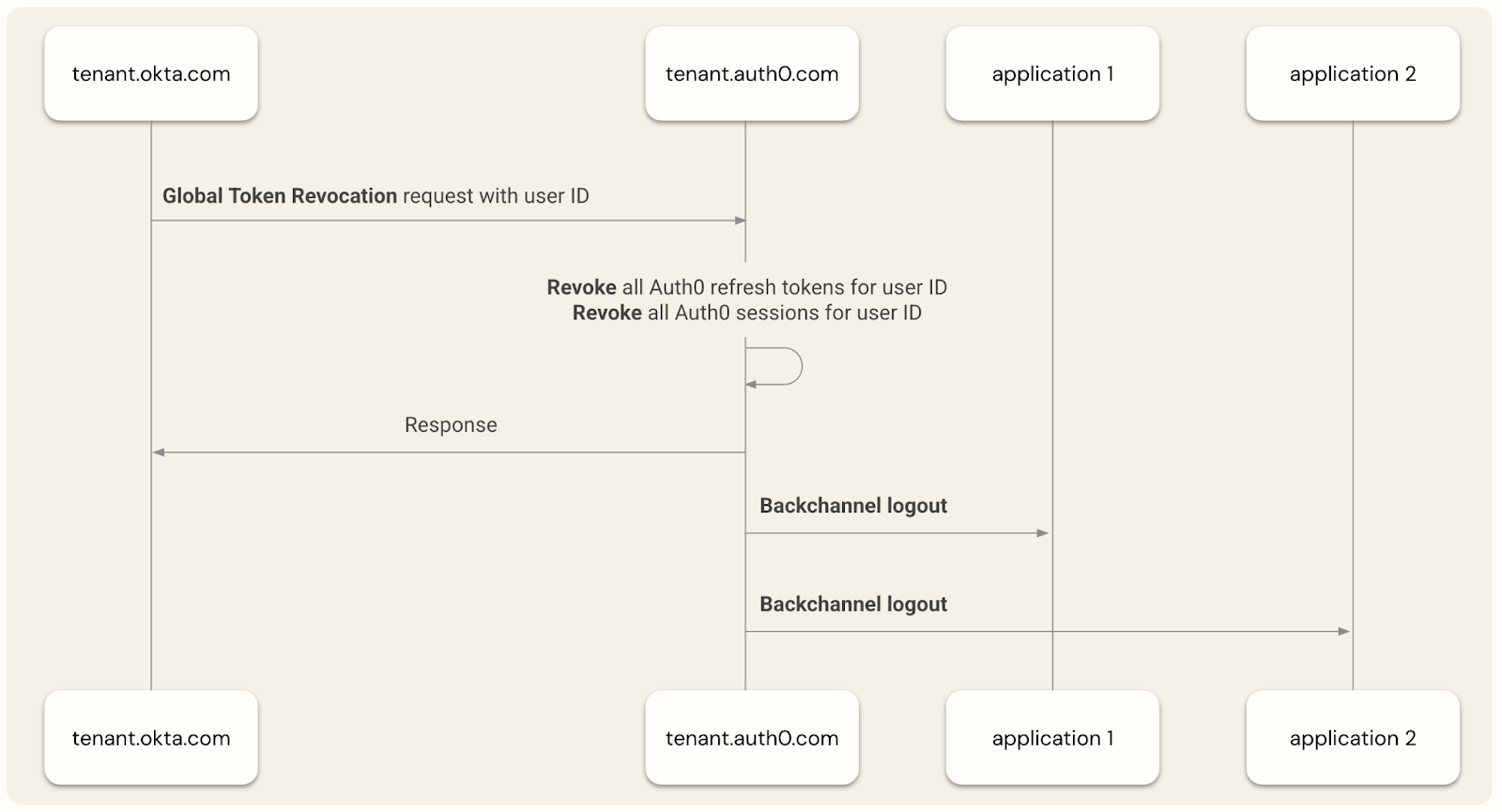
When Auth0 receives a logout request, it validates it using the same key set used to validate Okta Workforce Identity-issued ID tokens and SAML assertions. It then terminates all Auth0 sessions for the user, revokes Auth0-issued refresh tokens, and if configured, triggers OpenID Connect back-channel logout to revoke application sessions, as the following diagram shows:
Immediate Security Benefits for Apps Using Refresh Tokens and Auth0 Sessions
Auth0 supports various application architectures via OpenID Connect and OAuth 2.0 identity standards and its quickstarts and SDKs. This includes:
Traditional Web applications that create their own application sessions and may use refresh tokens and access tokens to access APIs through a secure backend. \
Browser-based JavaScript applications that leverage the Auth0 session layer or refresh tokens to get access tokens to access APIs within a Web browser. \
Native or Mobile applications that don’t run in a Web browser use refresh tokens and access tokens as the primary method of keeping users signed in.
Applications that use refresh tokens or leverage Auth0 sessions get these security benefits when the Universal Logout integration is enabled:
For browser-based apps that leverage the Auth0 session, the user loses access the next time the application polls the Auth0 session, and Auth0 prompts the user to sign in again when redirected
For apps that use refresh tokens, the user loses access as soon as their current access token expires, which can range from a few seconds up to the maximum access token lifetime configured in Auth0.
Among applications that federate with Okta WIC today, a majority use either the Auth0 session layer or refresh tokens to get new tokens and keep users logged in.
Instantly Revoke Application Sessions Using OIDC Back-Channel Logout
Web applications that create their own sessions can use Auth0’s existing OpenID Connect back-channel logout feature to instantly terminate them when Auth0 receives a Universal Logout request.
To learn more, see the Auth0 SDKs and Implementation Examples.
By integrating Universal Logout, developers using Auth0 can easily adopt the latest security standards for their B2B SaaS apps and offer them to their customers who use Okta Identity Threat Protection.
Customers who use Okta Workforce Identity to grant their employees or partners access to Auth0-integrated applications can benefit from the improved security posture that Universal Logout provides.
Included in Your Auth0 Subscription at No Extra Cost
Support for Universal Logout is included in all Auth0 subscriptions that include the Okta, SAML, or OpenID Connect connection types, including Enterprise, B2B Professional, B2B Essentials, and for all plans that include the Okta connection (B2C and Free).
What’s more, usage of the Okta Workforce Enterprise Connection does not count towards the Enterprise connection limit. Customers are free to enable Universal Logout for as many Okta Workforce integrations as they need, subject to the other limits of their subscription.
Learn More
You can learn more about Okta Identity Threat Protection and Universal Logout Integration with Auth0 by reading our product documentation here:
Disclaimer: This article may contain hyperlinks to non-Okta websites that are created and maintained by third parties who are solely responsible for the content on such websites.
About the author

Aaron Smalser
Principal Product Manager
