Data security is the process of protecting sensitive information from unauthorized access. It includes all of the different cybersecurity practices you use to secure your data from misuse, like encryption, access restrictions (both physical and digital), and more.
Data security has always been important. But since more people are working remotely as a result of the current health crisis (and cloud usage has skyrocketed to match), there are more opportunities for unauthorized access to your data than ever before.
And hackers ARE taking advantage of it. Interpol and the U.S. Chamber of Commerce, for example, are both reporting a massive increase in the occurrence of cyberattacks since the pandemic began.
So, no matter what your organization does, if it processes personally identifiable data (PII), improving your data security is an absolute must for 2021 (and beyond). Here’s everything you need to know about data security for your organization, including top threats, legal compliance requirements, and best practices.
Why Is Data Security Important?
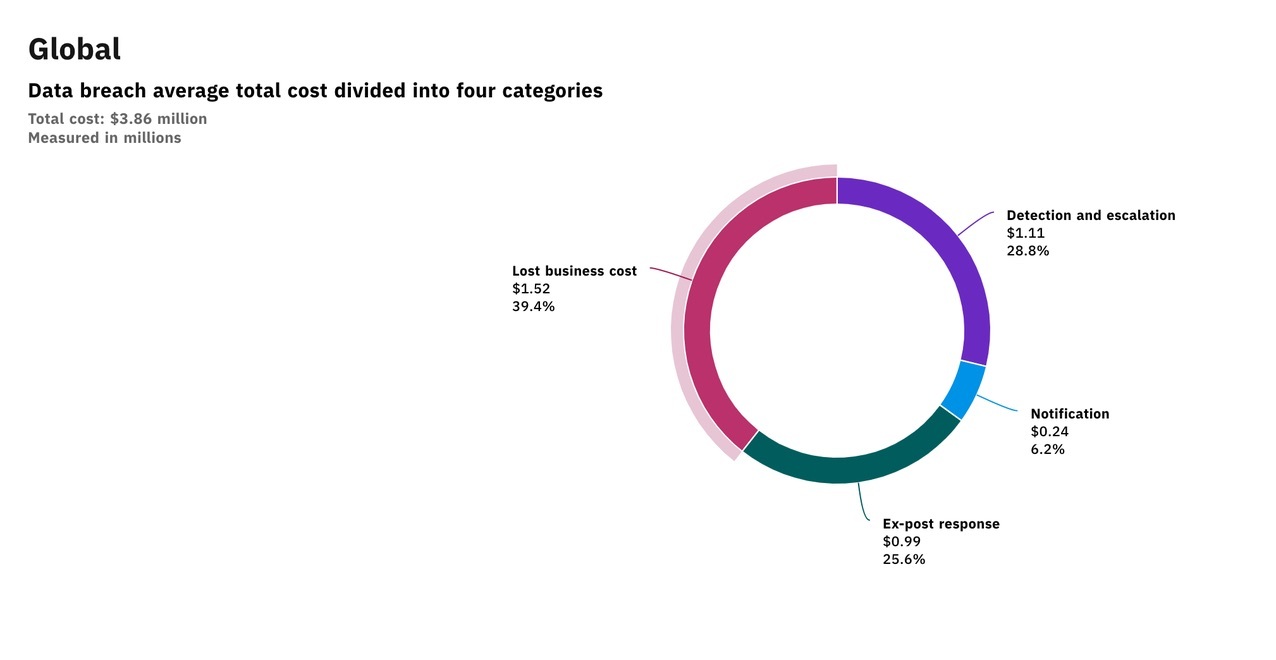
Data security matters because a breach can have serious repercussions for your organization. First and foremost, that often means financially — $3.86M for the average data breach in 2020, according to IBM and The Ponemon Institute:
The largest portion of the direct costs associated with a data breach comes from the loss of business that follows. However, 71% of CMOs agree that the top impact of a breach is how it affects brand equity and brand value.
According to Interbrand, a brand valuation agency, a large part of a brand’s value comes from “the role the brand plays in purchase decisions.” In other words, strong brand equity can actually enhance your customers’ willingness to pay for your products or services.
But it also means poor brand equity can have the opposite effect. And since studies show that 65% to 80% of consumers will lose trust in a company that’s leaked their data (a major hit to brand equity), the potential impact a breach can have could affect your brand for years to come.
The actual effect a loss of trust has on your brand image is highly dependent on the details of the breach, how it affects the customer, and more. But the takeaway is that a loss of trust can have a lasting impact on your business for years to come — even if you had a strong brand before it occurred (like Target did).
Data Security vs. Data Protection vs. Data Privacy
Data security is often confused with similar terms like “data protection” and “data privacy” because they all refer to ways to secure your data. However, the difference between these terms lies in the reasons for securing that data in the first place, as well as the methods for doing so:
- Data security refers to protecting your data against unauthorized access or use that could result in exposure, deletion, or corruption of that data. An example of data security would be using encryption to prevent hackers from using your data if it’s breached.
- Data protection refers to the creation of backups or duplication of data to protect against accidental erasure or loss. An example of data protection would be creating a backup of your data, so if it was corrupted (or if a natural disaster destroyed your servers), you wouldn’t lose that data forever.
- Data privacy refers to concerns regarding how your data is handled — regulatory concerns, notification, and consent of use, etc. An example of data privacy is gaining consent to collect data from website visitors by using cookies.
Data Security Compliance and Regulations
Most countries have strict data security regulations that companies must follow. And the consequences for violating them can result in major fines.
Unfortunately, regulatory compliance is often difficult to navigate, as requirements change from country-to-country (or region-to-region in some countries like the United States) and in relation to the kind of data you’re processing. So one of the best things you can do is to ensure you have knowledgeable counsel on hand who can help you navigate your legal requirements.
However, here are some of the most important and wide-reaching data governance regulations that could affect your organization.
General Data Protection Regulation (GDPR)
The GDPR is the European Union’s data protection and privacy law. It was passed in 2016 (and implemented in 2018) to protect consumers and unify the regulations regarding the management of their data for domestic and international businesses.
The GDPR requires any organization that processes personal data to implement the “appropriate technical and organizational measures” to protect that data (including acquiring an individual’s consent to store it and use it). This means requesting consent from users to collect their data, anonymizing that data to protect users in the event it’s breached, and following specific guidelines for notifying users in the event that a breach occurs.
Health Insurance Portability and Accountability Act (HIPAA)
HIPAA is the United States’ data security and protection law for regulating electronically protected health information (ePHI). It was passed in 1996 to control and modernize individual health data management, including fraud and theft protection standards, how insurance companies can and can’t use it to charge individuals for their services, and more.
HIPAA requires specific technological, physical, and administrative safeguards for any company that processes ePHI. Violations can range from $100 to $250K and up to 10 years in jail.
Sarbanes-Oxley Act (SOX)
The Sarbanes-Oxley Act was passed in 2002 to better protect corporate investors from fraudulent financial activity. It was created in response to a number of prominent corporate accounting scandals (Enron, for instance) and designed to increase the penalty for inaccurate or incomplete financial reporting (including tampering with financial data to present it a certain way). It also includes regulations around managing access to corporate financial information.
SOX mostly applies to public corporations and the way they disclose financial information. But there are a number of elements that also apply to private companies as well — for example, falsifying financial records or retaliating against employees who report financial crimes.
Federal Information Security Management Act (FISMA)
FISMA was passed in 2002 to standardize the way United States federal agencies handle their data. It requires that any federal agency (and any business from the private sector that works as a subcontractor/service provider) to follow strict information security policies (FIPS 200) and auditing procedures to ensure that they are followed.
The Top Threats to Data Security
When people think about threats to data security, the first thing that often comes to mind is a hacker breaking into your servers. But the reality is, the top threats to data security are often internal and a result of the unsafe behaviors of your employees.
For example, IBM and The Ponemon Institute studied the root causes of data breaches in 2020 and found that the top two causes were compromised credentials (often due to weak passwords) and cloud misconfigurations (leaving sensitive data accessible to the public):
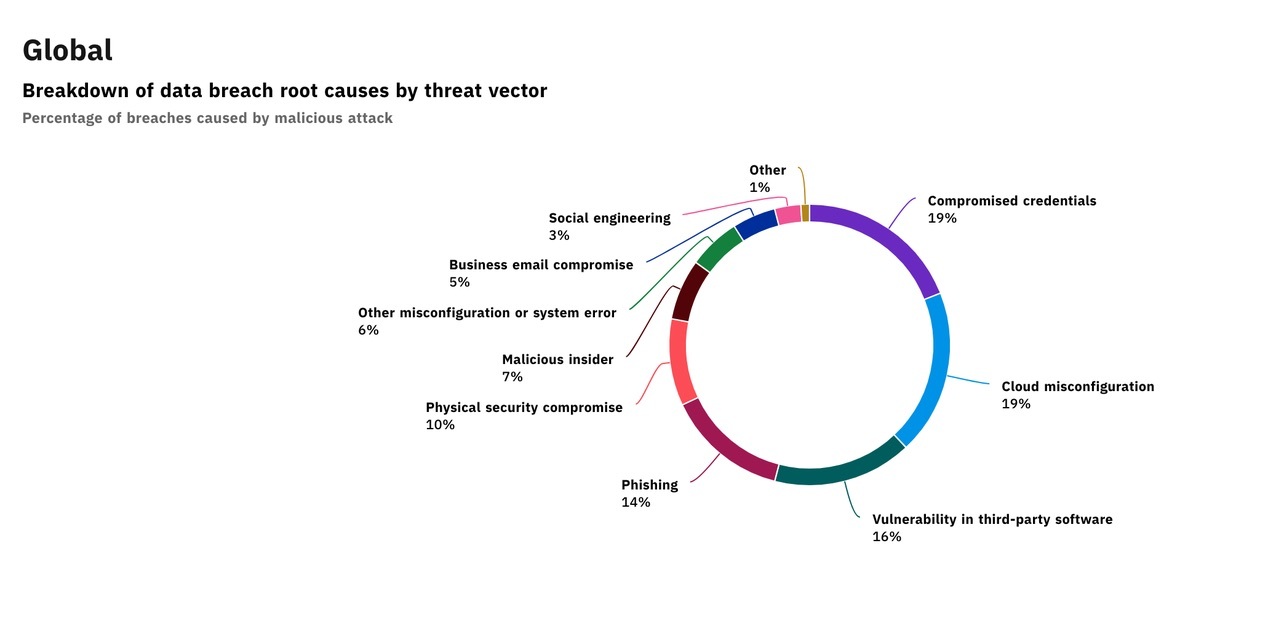
Courtesy of IBM/Ponemon Institute
One of the other top causes of data breaches (phishing scams) is also something the right employee training could prevent. IBM’s research shows that teaching employees how to spot phishing emails and other social engineering attacks would help reduce data breaches by 17%.
All that to say, while technologies like firewalls are important for protecting your data against security threats, your teams’ vigilance might be even more so.
Types of Data Security Technologies
There are several different technologies you can use to secure your data. You’ll want to use as many as you can to make sure all potential access points are secured.
Authentication
Authentication is the process of verifying a user’s login credentials (passwords, biometrics, etc.) to make sure it’s really them. And it’s one of the most important parts of your data security strategy because it’s a frontline defense against unauthorized access to sensitive information.
Authentication is conceptually simple but very difficult to get right at scale from a technological standpoint. However, new technologies like single sign on (SSO), multi-factor authentication (MFA), and breached password detection are making it easier than ever to secure the authentication process without sacrificing the user experience.
Encryption
Data encryption scrambles sensitive information with an algorithm so that it can’t be read by someone without the specific information (the encryption key) required to unscramble it. It’s an incredibly important data security tool because it ensures that even if someone gains unauthorized access to your information, they won’t be able to use it. You should always ensure that your encryption keys are stored securely and that access to them is limited to as few people as possible.
Tokenization
Tokenization is similar to encryption. However, instead of scrambling your data with an algorithm, tokenization replaces that data with random characters. The relationship to the original data (the “token”) is then stored in a separate protected database table.
Data Masking
Data masking does not transform your data into an intermediate form but rather is achieved by “masking” your data’s characters with proxy characters. Software reverses it once it’s delivered to its end destination.
Physical Access Controls
Data access control is an important part of your data security strategy, as well. And while digital access control is often managed through authentication procedures (and limiting the number of authorized users who have access to your data), physical access control manages access to the physical locations where your data resides (a data center or your on-premises server rooms).
Physical access management controls include protective measures like key cards, biometric authentication measures like thumbprint recognition and retinal scans, and security personnel.
Best Practices for Ensuring Data Security
A comprehensive data security plan has a lot of moving parts, all working together in real-time to ensure your data is safe. And the specific implementation of your plan will depend on the size and structure of your organization’s computing systems.
So what follows here is not meant to be a step-by-step breakdown of everything you need to do to create perfect data security; it’s an overview of the heavy-hitting concepts that come together to create a good foundation for data security.
Secure Your Information
An essential part of data security is securing your data where it’s stored. Here are three best practices for improving the security around the places you store yours both digitally and physically:
- Manage access to sensitive information. Managing who has access to your data based on their user ID is a great way to keep sensitive information restricted to only those who need to see it. This limits the amount of damage that can be done if someone’s username or login details are stolen.
- Encrypt everything. Encryption is one of the best tools that you have to keep data safe. It helps you ensure that hackers can’t use any information they might get ahold of. You should also make sure you encrypt transmissions to add another layer of security to any information you send.
- Protect user data at the source. When customers and employees log in for the first time (or repeated times), you can verify and secure their information with secure authentication practices like social login. This not only simplifies the process and reduces the risk of churn, but it also helps organize all of their sensitive data in a single location instead of in multiple databases and spreadsheets that can easily be lost.
Prepare For Threats
Cybersecurity threats are constantly evolving and changing because hackers are always looking for gaps in your security systems. So data security isn’t a “set it and forget it” activity — it’s an everyday activity.
Here are the top ways to prepare for potential attacks (and the aftermath of any breach that occurs):
- Test your system(s). The best defense is a good offense, and the best offense in secure data recovery is working to ensure you don’t lose your data in the first place. But while automation can help you monitor your systems, it simply cannot match the creativity of a human being trying to break in. So it’s best to either create an internal team to stress-test your systems or find someone outside your company to do it.
- Educate your employees. Common data security attacks like spear-phishing emails and USB traps target employees who are unaware of the risks and have let their guard down. Circulating everyday tips like those from Proofpoint or implementing Inspired eLearning’s executive training can go a long way toward mitigating these risks.
- Have an incident management plan. Having a comprehensive response plan for instances where your data is compromised can significantly limit the impact it has on your organization. Yes, IT needs to be aware of what to do, but you should also create guidelines for management, letting employees know, and next steps for recovery. (See how Reddit handled their recent breach.)
- Create a secure data recovery plan. In case of corruption or the unhappy scenario where something you need has been deleted or compromised, it’s important to be prepared to deal with it. For many teams, this means having a backup copy of critical data that is regularly updated. The backup itself will have to be protected and should also be separate from the rest of your data.
Delete Unused Data
There will come a time when your data becomes outdated or is no longer in use. It’s important to get rid of that data when this happens because it could still harm your users if it were to be breached.
Take your users’ old passwords, for example — since 65% of people reuse their passwords across multiple sites, an old password could still be used to breach their data at another company if they haven’t changed it on all of their digital accounts.
Here are two best practices for deleting unused data:
- Know how and when to let go. When it’s time to get rid of digital information, you need to dispose of it properly. When you have to throw out sensitive information on paper, you shred it. You cut up your credit cards and write “VOID” on checks before disposing of them. Digital data is no different. Make sure that when you’re wiping information, it’s really gone and not lingering somewhere that will come back to bite you.
- Don’t forget physical copies. If any of your backups are on paper, are stored on a thumb drive, are X-rays or microfilm or negatives — or anything else that’s physical and totally separate from your digital systems — don’t forget about them. When you’re deleting unused information, make sure part of your process is double-checking to see whether that information has a physical counterpart and, if so, destroying it in kind.
Run Compliance Audits
There are standards that can help lower your risk of a data breach. There are also a few regulations you’re likely required to follow by law that will help you do the same thing.
The regulations that apply to your business will depend heavily on industry and location, so you’ll need to do your homework to assess which ones those may be. But if you’re processing personally identifiable information, it’s in your best interest to audit yourself and ensure your business is in compliance.
Not only will this keep you out of legal trouble, but it can significantly improve your data’s security.
Don’t Forget Mobile Data Security
In the first half of 2018 alone, mobile attacks hit 150 million — and rose another 30% in 2019, according to McAfee’s 2020 Q1 Mobile Threat Report. And as mobile cyberattacks increase, mobile security becomes an even more critical part of your data security strategy.
There are several steps you can take to enhance your mobile data security:
- Regularly update all apps to protect against spyware threats.
- Delete inactive apps. (Providers could have suspended or removed access to them due to a security breach.)
- Before downloading new apps, check the list of permissions requested. If these seem too invasive, employees should skip the download because it could contain mobile malware.
- Create unique passwords for every new mobile account. Never default to standard logins.
- Use communication apps that encrypt data transfers to restrict access.
- Require multi-factor authentication to access internal tools.
- Make sure employees know how to access their devices remotely. If a device is lost or stolen, being able to quickly delete or transfer information is critical.
However, keep in mind that mobile data security isn’t just for smartphones and tablets. It now includes other mobile devices such as smartwatches and another wearable tech, video conferencing tools, and other workplace productivity tools, too.
Data Security Depends on Humans
Your employees are the frontline for the security of your data now more than ever. So encouraging the right behaviors is essential to ensuring that a breach doesn’t happen to your business.
One of the best ways to do that is to create a better user experience for your team. A simplified user experience makes it much easier for them to follow cybersecurity best practices, like using unique passwords for each application or using longer, more complex passwords (which are harder to guess or crack).
Auth0 makes it easy to build a streamlined authentication experience for your entire business. Learn more about Auth0 here.
About the author

Diego Poza
Sr Manager, Developer Advocacy (Auth0 Alumni)