Identity is one of the most critical — and misunderstood — parts of modern application architecture. As organizations scale from B2C to B2B, adopt enterprise SSO, or introduce more advanced security controls, misconceptions about what identity platforms can and cannot do often shape technology decisions more than reality.
Auth0 is no exception. Over the years, a number of myths have circulated about its suitability for B2B use cases, multi-tenancy, single sign-on (SSO), authorization, and long-term flexibility. Many of these claims are based on outdated assumptions or incomplete information — they can lead teams to overestimate complexity, underestimate capabilities, or delay becoming enterprise-ready.
In this article, we’ll address some of the most common myths about Auth0 head-on and clarify how the platform actually works today. Whether you’re building a B2C application that’s expanding into B2B, or preparing your product to be enterprise-ready, the goal is simple: to separate myth from reality.
Myth 1: Auth0 Wasn’t Designed for B2B Multi-Tenancy
One of the most common misconceptions about Auth0 is that it was designed primarily for B2C use cases and lacks meaningful support for B2B multi-tenancy. According to this view, supporting multiple customers requires higher pricing tiers and extensive custom development.
Reality
Auth0 was built with B2B use cases in mind. Organizations are a first-class feature of the platform, enabling true multi-tenancy without relying on workarounds such as custom metadata or duplicated tenants. Features like organization-aware authentication flows, role assignment at the organization level, enterprise SSO, and SCIM provisioning are all natively supported — no custom code required. You can get started with Organizations on our B2B Free (self-service) or Essential plan.
Many companies that started using Auth0 for B2C were able to pivot into B2B offerings almost instantly — becoming Enterprise ready is possible by doing little more than configuring an OpenID Connect (OIDC) connection and toggling it on for your application. That’s the power of having turnkey identity infrastructure in place.

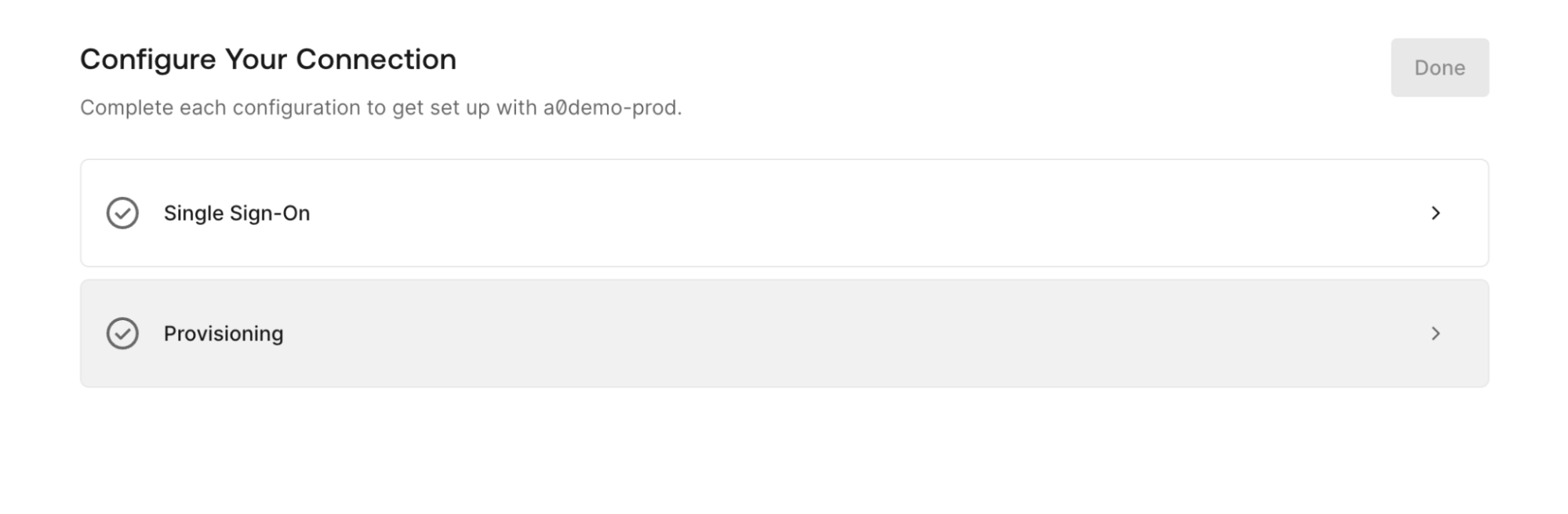
Myth 2: Self-Service SSO Requires Tons of Custom Code
Another frequent claim is that offering self-service SSO requires wrapping Auth0 with large amounts of custom logic that is difficult to implement and even harder to maintain.
Reality
Auth0 provides Self-Service SSO out-of-the-box. Your B2B customers can configure, test, and enable their own Enterprise Identity Provider. This significantly reduces operational overhead for both vendors and customers, while improving onboarding speed and autonomy.
In addition, Auth0 supports Self-Service User Provisioning for System for Cross-domain Identity Management (SCIM), enabling automated provisioning and deprovisioning with minimal effort.
This isn’t a “build your own portal” scenario — it’s turnkey.
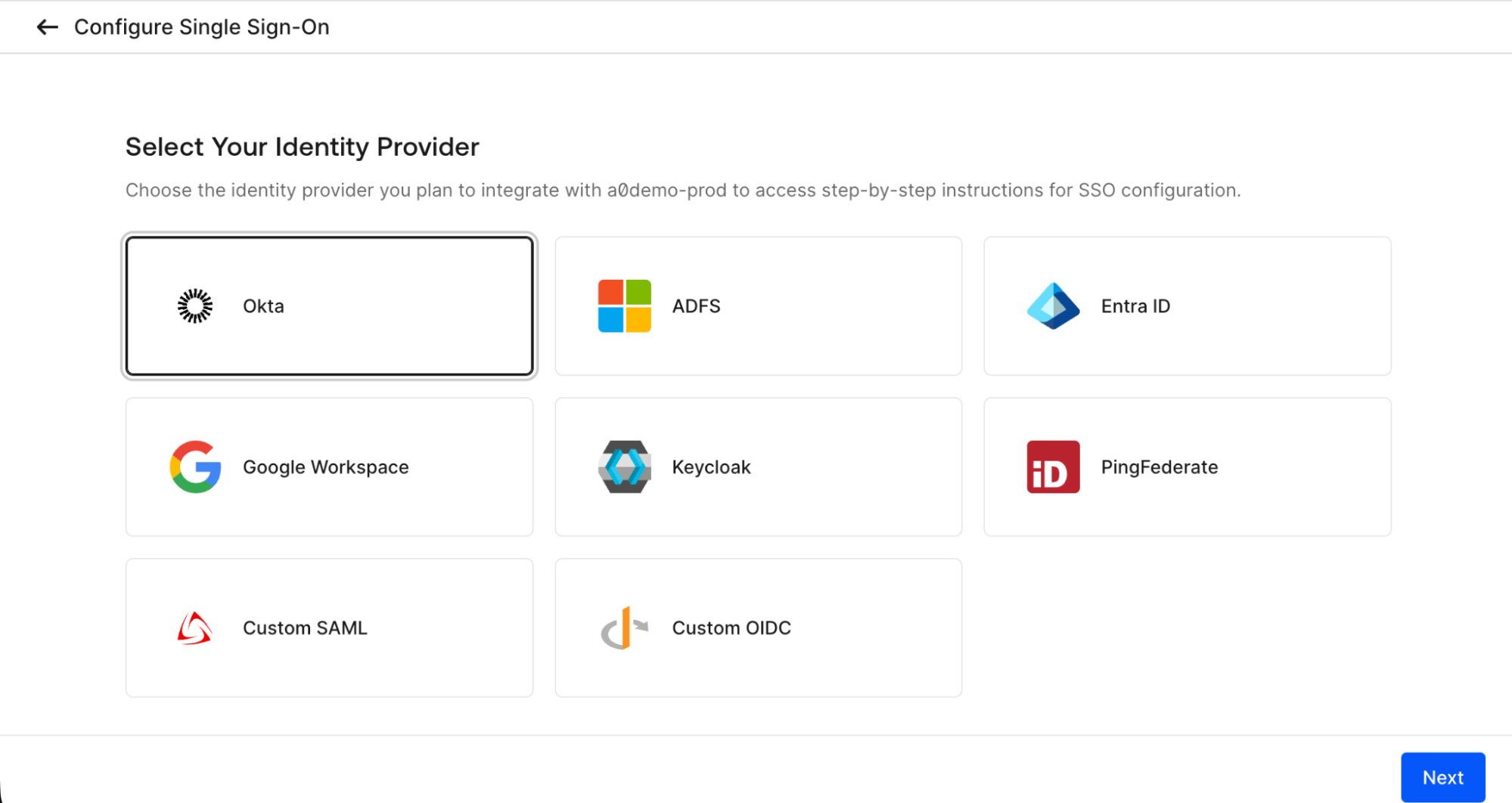
Myth 3: SSO Configuration Is Rigid and Time-Consuming
Some believe that SSO in Auth0 is rigid, difficult to configure, and only accessible on higher-tier plans, limiting its usefulness for growing teams.
Reality
In practice, cross-application SSO in Auth0 works out of the box and requires no additional configuration. When you create a second application, you simply enable the same connection used by your first application, and cross-app SSO works automatically.
There is no requirement to write custom code, and enabling cross-application SSO involves minimal setup. This capability is not limited to the Enterprise plan — you can get started with cross-app SSO on both the B2C and B2B Professional plans.
If your customers expect a seamless experience across multiple applications, Auth0 enables cross-app SSO quickly and sustainably.
Myth 4: Auth0’s Authorization Model Is Too Limited and Hard-Coded
Another misconception is that authorization in Auth0 requires hard-coded logic and offers little flexibility when assigning roles or permissions.
Reality
Auth0's Role-Based Access Control (RBAC) model handles the majority of authorization needs without any hard-coding. You can define permissions, group them into roles, and assign those roles to users — all through the dashboard or APIs. As your application grows, these assignments can be automated through workflows or adjusted dynamically based on your business logic.
Need more flexibility? Auth0 Actions let you customize authorization behavior at runtime, so you can adapt access control logic as requirements evolve without rewriting application code.
For scenarios requiring fine-grained, relationship-based access control — like hierarchical organizations, resource ownership, or contextual permissions — Auth0 Fine-Grained Authorization (FGA) provides a dedicated solution for modeling complex authorization logic.
The key insight: you start simple with RBAC and expand capabilities only when your use case demands it.
Myth 5: Risk-Based MFA Is Limited and Difficult to Customize
Fraud detection and adaptive multi-factor authentication (MFA) are often assumed to require external systems, complex orchestration, or significant custom infrastructure to implement correctly.
Reality
Auth0 ships with built-in risk signals, threat intelligence, breached-password detection, and Adaptive MFA controls that automatically adjust authentication requirements based on contextual risk. Factors such as device behavior, IP reputation, location anomalies, and login patterns can be used to prompt for MFA only when risk is detected, helping balance security and user experience.
For teams that want to incorporate external fraud or risk services, Auth0 makes this straightforward through multiple extensibility options, including:
- Auth0 Actions which run directly in the authentication pipeline
- Marketplace integrations with third-party fraud and risk providers
- Prebuilt, drag-and-drop Actions (such as country-based access control)
Need to call a third-party risk engine before allowing a login or triggering MFA? You can do that directly inside an Auth0 Action — no separate AWS Lambda or external orchestration required.
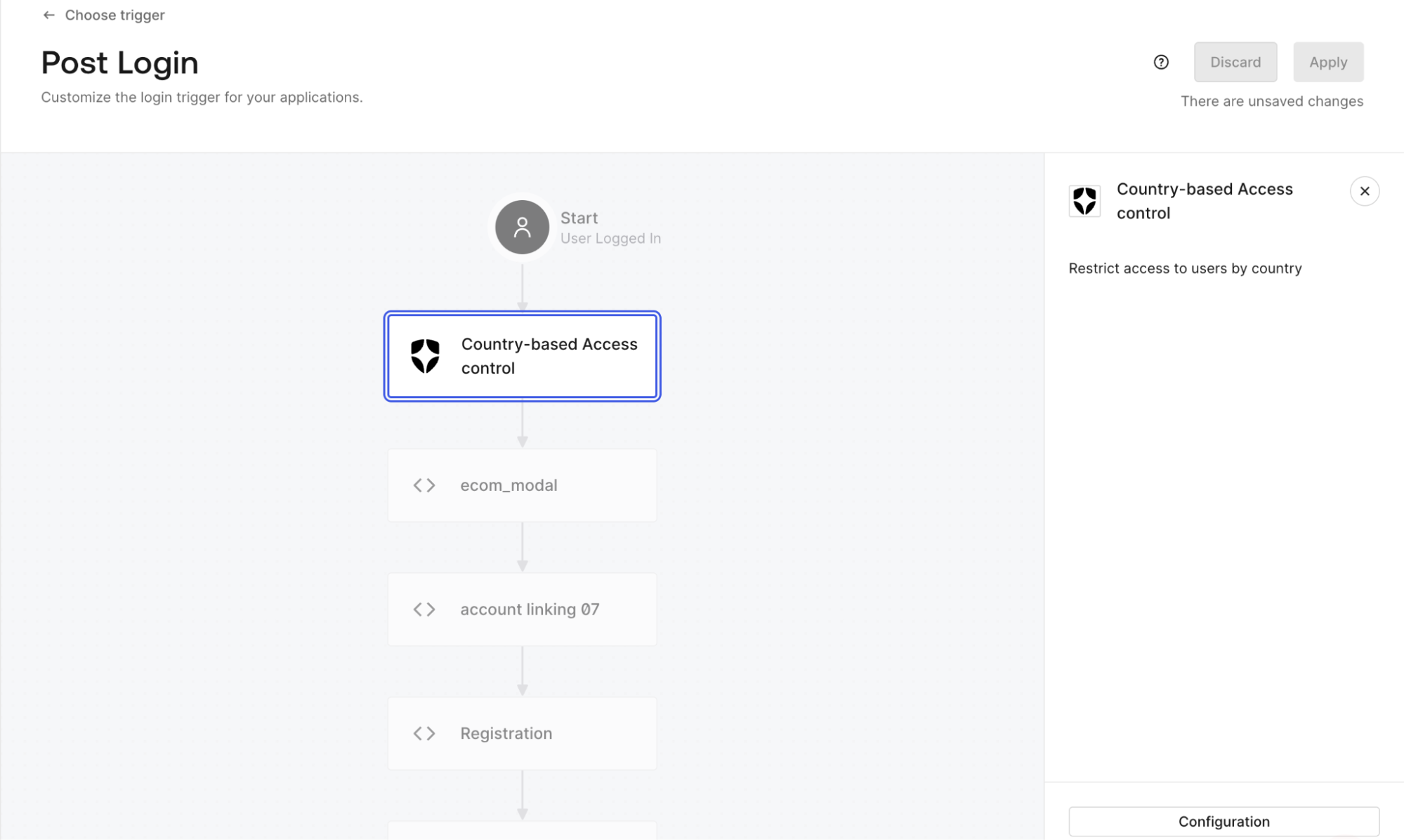
Myth 6: Custom User Journeys Require Building and Maintaining Your Own UX
Authentication flows can get complicated — signup, password reset, invitations, progressive profiling, and more. Some assume these require building a full identity UX layer in-house.
Reality
Auth0 provides all core user journeys out of the box: login, sign-up, password reset, invitations, organization-based access, and more. Once an application is integrated, Auth0 manages these flows without requiring ongoing custom development from the application team.
For scenarios that require additional customization, Auth0 Forms enables teams to extend user journeys with capabilities like progressive profiling, verification steps, account linking, or acceptance of terms and conditions. These customizations can be introduced without forcing teams to build and maintain entirely custom flows.
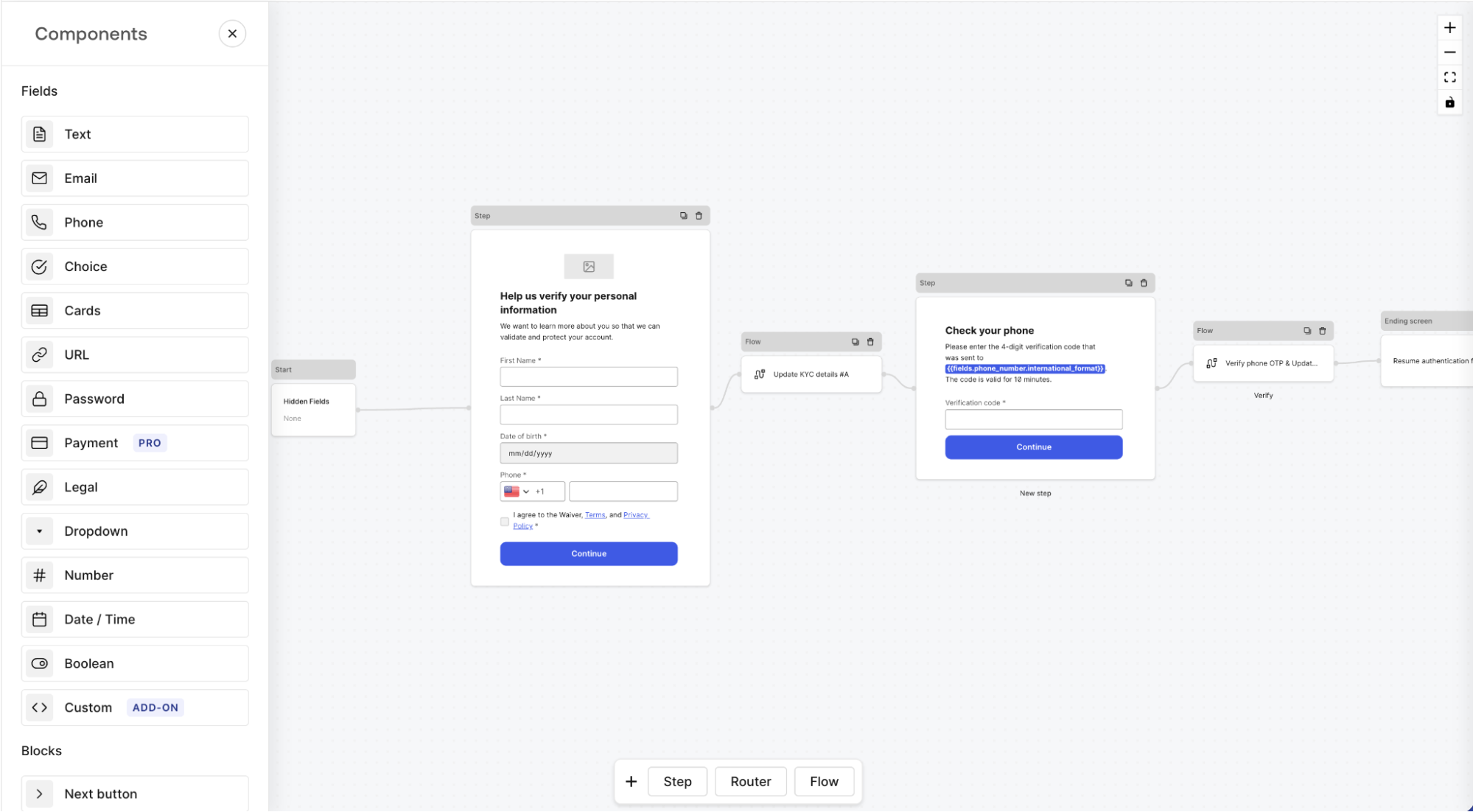
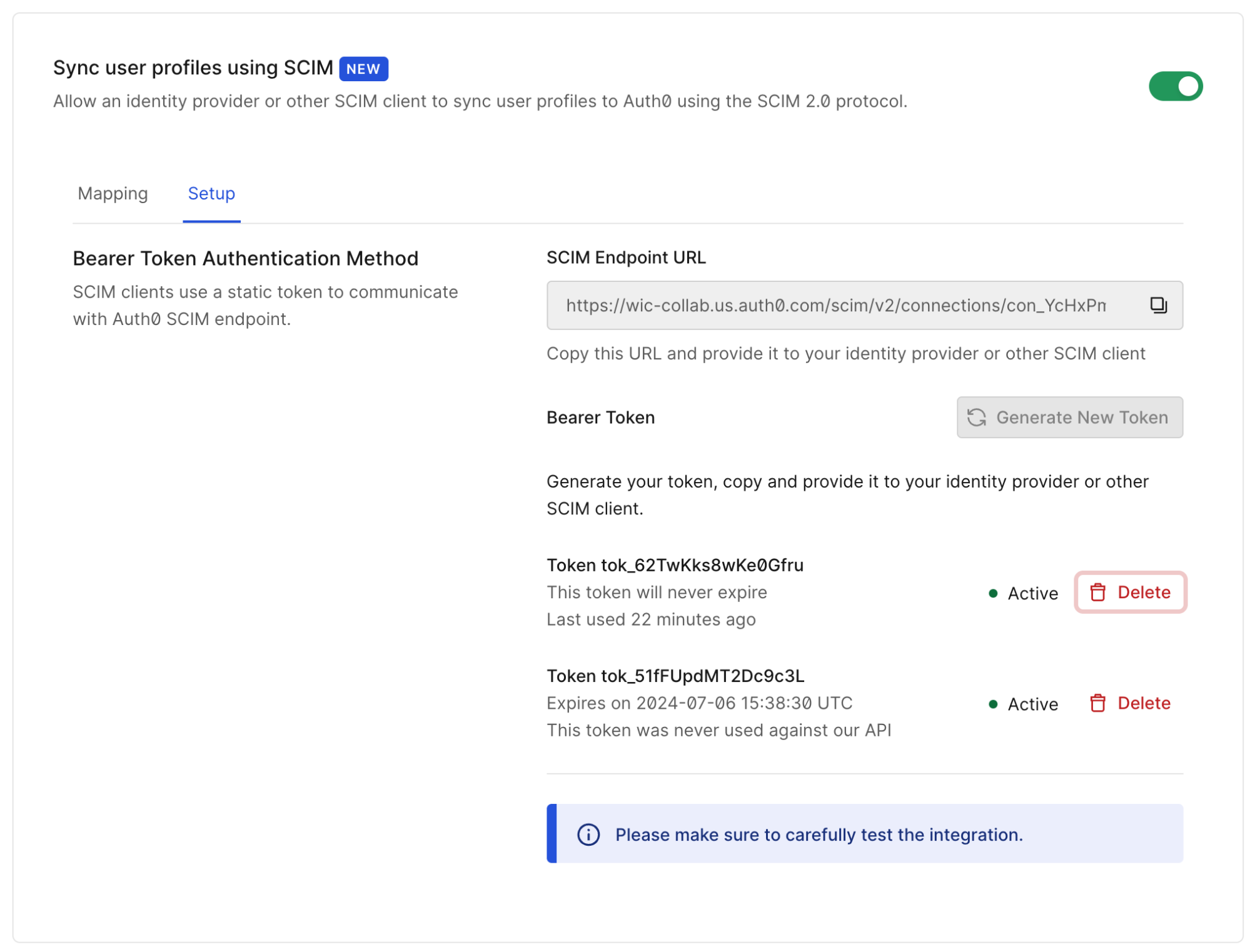
Myth 7: SCIM Provisioning Is Only Available on Expensive Plans and Requires Heavy Customization
SCIM provisioning is often perceived as an expensive, complex feature that requires significant customization to work with enterprise identity systems.
Reality
Inbound SCIM is available on the B2B Essential, Professional, and Enterprise plans. Configuration is straightforward and integrated directly into enterprise identity connections.
Auth0 also offers Self-Service SCIM, which allows B2B customers to manage their own provisioning configuration. This capability significantly reduces operational overhead and support burden for application teams.
Instead of building one-off provisioning scripts or relying on manual onboarding processes, Auth0 provides SCIM provisioning as a turnkey, out-of-the-box capability.
Myth 8: Updating User Journeys Requires Slow, Code-Heavy Changes
There’s a perception that evolving authentication flows requires rewriting configuration, pipelines, or user interfaces.
Reality
Once an application is integrated with Auth0, most changes no longer require updates to the application’s codebase. Auth0 continuously ships new functionality — from security improvements to new authentication methods — without forcing teams to redesign their implementations.
Identity evolves quickly. Auth0 consistently leads innovation in response to new security threats, regulatory requirements, and expanding business needs, helping teams future-proof their authentication and authorization strategy.
Identity That Scales With You
Many of the myths about Auth0 reflect outdated assumptions rather than current reality. From B2B multi-tenancy and self-service SSO to flexible user journeys, adaptive MFA, and a future-proof identity strategy, Auth0 is designed to scale with your business as requirements evolve.
By understanding what the platform provides out of the box — and where it offers extensibility when needed — teams can make informed decisions without over-engineering or unnecessary complexity. When identity decisions are grounded in facts rather than folklore, teams can build secure, scalable applications and become enterprise-ready with confidence.
About the author

Stanley Varner
Senior Solutions Engineer
I’m a Senior Solutions Engineer at Okta, partnering with organizations to design and implement secure identity and access management solutions that deliver seamless user experiences. Having launched and managed my own e‑commerce sites and helped build a SaaS fitness‑coaching platform, I’ve learned to anticipate real‑world business challenges and architect IAM solutions that scale.
When I’m not geeking out on OAuth flows, you’ll find me spending time with my family, working out, or experimenting with my next side project.
