The saying goes, “If it ain’t broke, don’t fix it,” and plenty of CISOs and CTOs live by that motto when considering whether to update or outsource a particular functionality. But when it comes to Identity and Access Management (IAM), just because your old system is still up and running, doesn’t mean it’s working as it should.
At best, an outdated IAM solution could be leaving money on the table by failing to fully take advantage of user data. At worst, it could be leaving your company vulnerable to potentially disastrous data breaches and regulatory fines, and siphoning off developer time that could be spent refining your core competency.
We’ll go over three of the hidden costs that lurk beneath the surface of in-house IAM solutions, and how real companies have reaped the benefits of investing in an alternative.
If You Don’t Deal With Data Security, It Will Deal With You
In recent years, data security has become an urgent issue for companies of all sizes, with 3,813 breaches reported in the first half of 2019 alone, exposing billions of records. The problem isn’t confined to a single industry or region, as evidenced by some of the most recent high-profile data breach stories:
Facebook has repeatedly been in the news for exposing user records, including an April 2019 scandal that exposed passwords the company had stored in unencrypted text.
A hacker broke into Australian graphic design company Canva, stealing 139 million records and tarnishing Canva’s reputation as a tech darling.
Europe has been rocked by numerous major breaches and equally major regulatory fines. The top ten GDPR fines for breaches in 2019 totaled €402 million.
Meanwhile, Latin America is grappling with its own epidemic of breaches. According to one 2018 study, three in five businesses in the region have had at least one security incident.
In response to these breaches and concerns about ethical data collection, new data privacy laws like GDPR and CCPA are springing up around the world.
All these laws seek to ensure that companies have appropriate security measures in place to safeguard personal data. IAM is at the heart of data privacy and security, and a sophisticated platform like Auth0 can save you money by protecting you from breaches and helping to manage your compliance obligations.
According to IBM, the average cost of a data breach is $3.92 million, and no company can assume they’re safe. A Verizon study found that 43% of all breaches in 2019 involved small businesses. One of the most serious cybersecurity threats of the moment are credential stuffing attacks, in which hackers use credentials stolen in one breach to log in to other accounts.
If these attacks lockout users (as in the Disney+ attack), they can be damaging, but if someone impersonates an admin, they can be downright devastating, and Auth0 detects over 50,000 credential stuffing attacks every day. Implementing multi-factor authentication (MFA) and breached password detection are the most surefire ways to ensure your users are who they claim to be, but these capabilities may be out of reach for a legacy IAM system.
Aside from the damage done by an attack itself, a lack of security can leave your business vulnerable to prosecution under data privacy laws. Under the EU’s GDPR, many businesses have been hit with significant fines for failing to implement identity-based security measures. For example, Dutch insurer UWV will have to pay €900,000 specifically for not having MFA in place for health data. A sophisticated IAM platform like Auth0 is continually evolving to meet the regulatory and cybersecurity challenges of the moment, while an in-house IAM solution may fall behind without constant maintenance.
“Just because your old identity system is still up and running, doesn’t mean it’s working as it should. How to avoid the high cost of doing nothing.”
Tweet This
Maintaining IAM Is a Costly Distraction to Your Team
Coding for identity and authentication in-house is a time-consuming (and therefore expensive) proposition for developers. Aside from maintaining legal compliance, integrating with new applications and third parties can be tricky, since most DIY IAM solutions weren’t designed with extensibility in mind.
While your in-house developers tinker with your system, you’re pushing back your time to market and keeping your partners and customers waiting. When you consider costs associated with those delays and missed opportunities, building IAM yourself simply doesn’t make sense; it’s like forcing a basketball team to sew its own sneakers. Now consider the alternative: outsourcing to IAM experts.
In contrast, implementing Auth0’s platform takes less than a month for 94% of customers, and according to Forrester’s research, Auth0’s customers reduce the time it takes to federate enterprise partners by 33%. For example, the automotive data services platform Otonomo started out with an in-house identity solution, but it became too difficult to manage as they grew. They switched to Auth0 and reported savings of at least $200,000 per year and a 10% reduction in development time. Similarly, Servcorp says that they save weeks using Auth0 rather than using their own in-house system when they are onboarding new applications.
Extensibility is particularly critical for companies in the M&A market, since quickly integrating data after a deal is crucial to identifying synergies and creating value, but without an extensible IAM solution, migrating data can take months. But a platform like Auth0’s can connect to any application, platform, or device. This allows for automatic migration from multiple databases, creating a single source of truth without slowing down normal operations.
An IAM solution’s ability to quickly integrate new features can make or break a business. Case in point: Apple recently announced that it would begin requiring every app in the App Store to Sign In with Apple. That means that every business with a mobile app has to incorporate this feature or lose their seat at the table. But if your team has to stop everything and focus on integration, your other projects, more central to your company’s value proposition, will inevitably fall by the wayside.
“Uncover the three of the hidden costs that lurk beneath the surface of in-house IAM solutions.”
Tweet This
IAM Should Be a Bridge, Not a Wall, Between You and Your Users
When you’re using a legacy IAM solution, it can feel like your company and its users are on either side of a brick wall. Users are frustrated by poor UX, and businesses are left in the dark about their users’ identities, needs, and behaviors.
Removing that barrier starts at the login box by making the experience both frictionless and secure. Achieving this requires a highly customizable IAM solution. If you’re still making your users enter a username and password combination every time they log in, you risk users forgetting their passwords and having to reset them, which is not the pleasant experience you want them to associate with your business. Users might also recycle the same password over multiple applications—the very behavior credential stuffing attacks take advantage of.
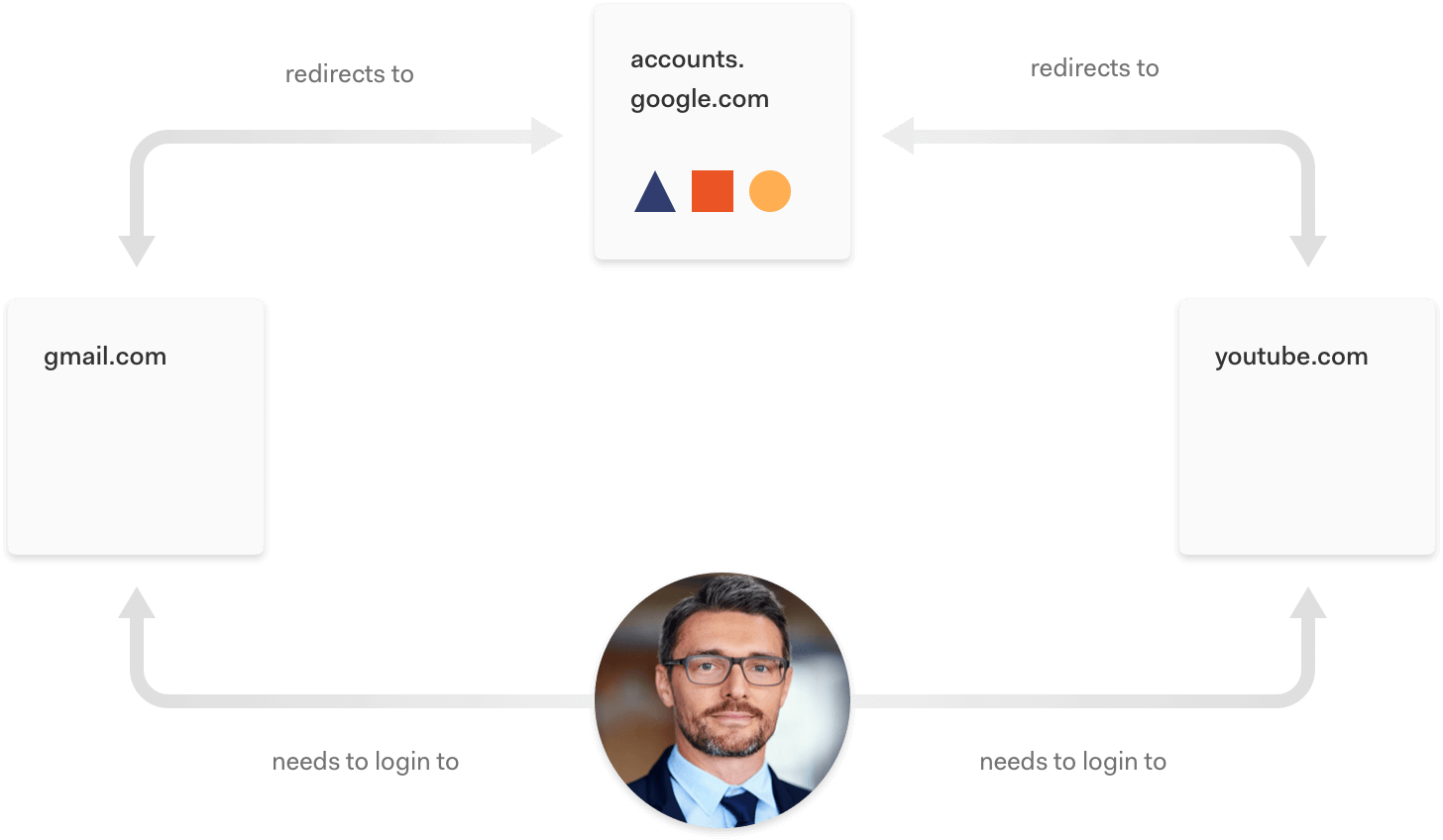
With a cutting-edge IAM platform, on the other hand, the login experience can create a single, holistic view of users. You can implement Single Sign On (SSO) and enable enterprise federation or social login. Users are familiar with the experience of a single login giving them access to multiple applications from companies like Google, which automatically logs users into all their connected accounts. It provides them with an easy experience, and for companies, it enables the creation of data-rich profiles, allowing you to visualize each step of a user’s journey.
Building security into authentication without compromising UX requires a highly customizable IAM solution. For example, it would be a mistake to implement MFA across the board; users don’t want to have to enter a one-time code every time they log in. But Auth0’s platform allows for step-up authentication, so with a few lines of code, your developers can define the specific parameters under which to request extra credentials. With this level of customizability, you can use security measures as a precise tool, not a blunt instrument.
The login box is the most visible part of IAM for your users, but a sophisticated IAM platform goes much further in organizing and protecting their data. Legacy IAM systems leave data siloed across multiple applications and mean that a single user might have multiple profiles. That makes it difficult to manage user requests, or even have a clear idea of where all their personal data is.
But Auth0’s platform offers the simplicity of a central dashboard, a single location from which you can manage user needs. If an employee starts or stops work, you can grant or revoke their access to sensitive data. From there, you can manage permissions with the flip of a switch. If the system flags a suspicious login, you can examine the circumstances and decide what action to take. And if users make a request to change or delete data, you can quickly comply, thus meeting your data privacy obligations.
Make IAM an Asset, Not a Drain
Most legacy IAM solutions were designed to be more or less static, but today, identity is evolving at breakneck speed. Without a cutting-edge IAM solution, your company will have to slam on the breaks every time a new data privacy law is passed, a new threat appears, and every time you want to embrace innovative new technologies.
If you don’t have an identity platform that evolves with you, you’re building these costs into your business plan. So while “If it ain’t broke, don’t fix it” may be an apt expression in certain contexts, IAM, a better adage is “An ounce of prevention is worth a pound of the cure.”
Digital transformation is a moving target for any company, but when choosing priorities to overhaul, consider that IAM sits at the nexus of security, analytics, and UX. If you’d like to learn more about how the right IAM solution can save your business money, time, and energy, don’t hesitate to reach out to the Auth0 team.
About the author

Martin Gontovnikas
Former SVP of Marketing and Growth at Auth0 (Auth0 Alumni)
Gonto’s analytical thinking is a huge driver of his data-driven approach to marketing strategy and experimental design. He is based in the Bay area, and in his spare time, can be found eating gourmet food at the best new restaurants, visiting every local brewery he can find, or traveling the globe in search of new experiences.View profile